Orphaned accounts are active accounts in applications, such as Active Directory, which do not have a corresponding account owner. Active accounts that don’t belong to a real user pose a potential security risk. These accounts may also result in unnecessary license fees. Virtually all of our customers have a need to be able to easily identify and manage orphaned accounts. In this post, we will explore how accounts can be orphaned and the tools available in OpenIAM to help you manage them.
How do accounts get orphaned?
There are several ways in which accounts get orphaned. These include:
- An employee leaves and their accounts in the various applications are not decommissioned
- Account in an application lacks sufficient information to allow us to link the account to a real user. Consider an account in Active Directory, where the record lacks an employee ID or similar attribute that would allow us to link the account to their corresponding record in the authoritative source.
- Service accounts that have not been decommissioned or reassigned to a new user, when the original owner leaves the firm
While there are other cases, orphaned accounts are largely able to thrive in the absence of a comprehensive identity solution.
How can orphaned accounts be identified?
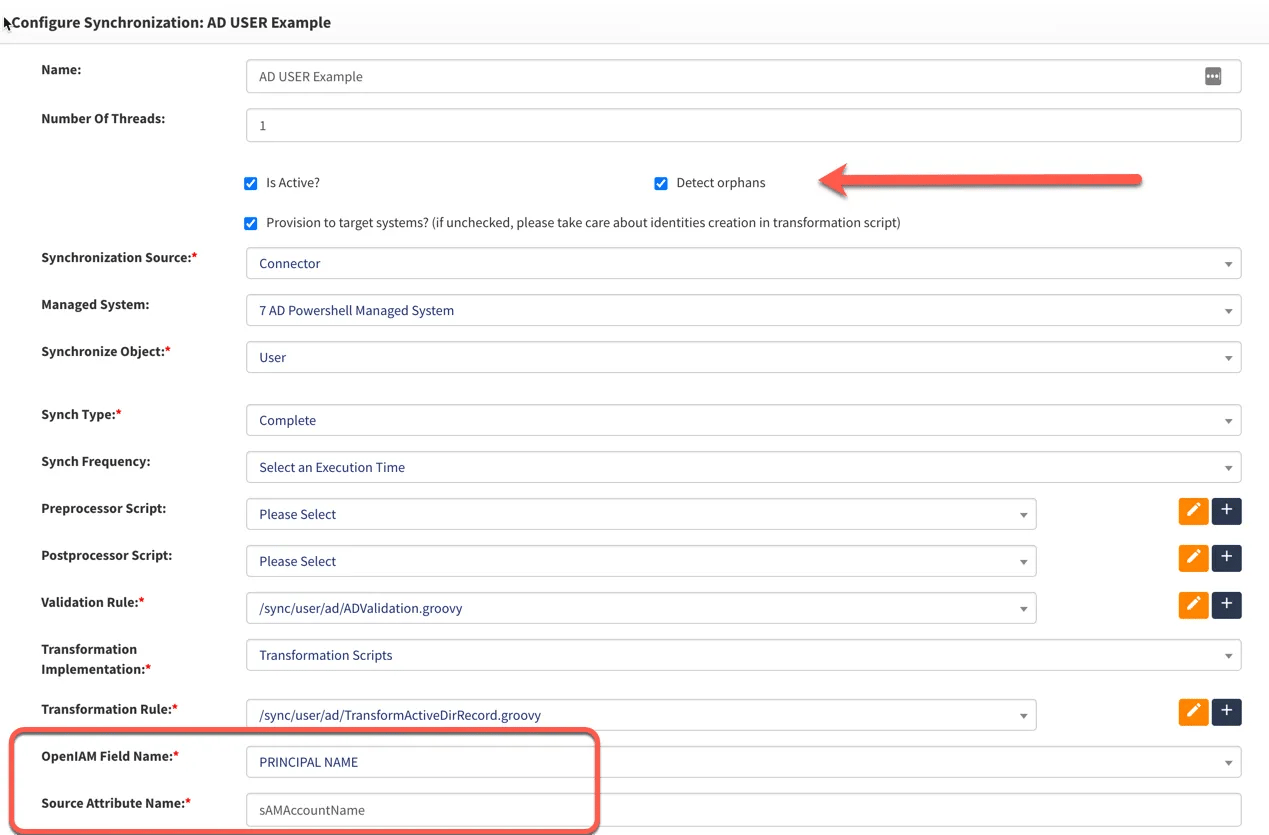
In OpenIAM connectors are used to integrate with applications. These connectors are used for provisioning, synchronization and reconciliation. Depending on your requirements, you can configure a synchronization or reconciliation task to run at regular intervals. If you are using synchronization, then you can enable the “Detect orphans” checkbox as shown below.
When a synchronization task is executed, data from the target application will be compared to the data in OpenIAM using the matching attributes shown in the configuration below. When a match fails, we can either:
- Create a new user in OpenIAM
- Log it as an orphan
If the “Detect orphan” checkbox is on, then an orphaned record will be created in OpenIAM.
In cases where a connector does not exist, then we can do the same using a feed from a CSV file.
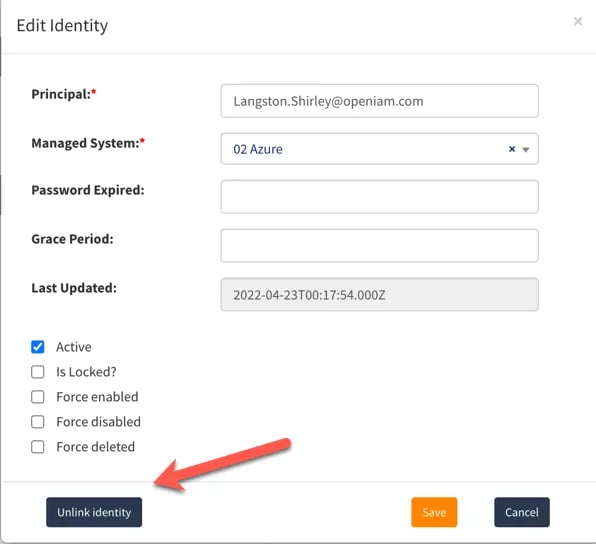
There is one more case where an orphan will be created. In the user manager, we can see all the accounts linked to a user’s profile. It possible to unlink an account from a user. In this case, the unlinked account will also appear as an orphan.
Managing orphaned accounts
In the user manager, there is a a menu option for “Orphan Management”. This interface can be used to view and manage orphans.
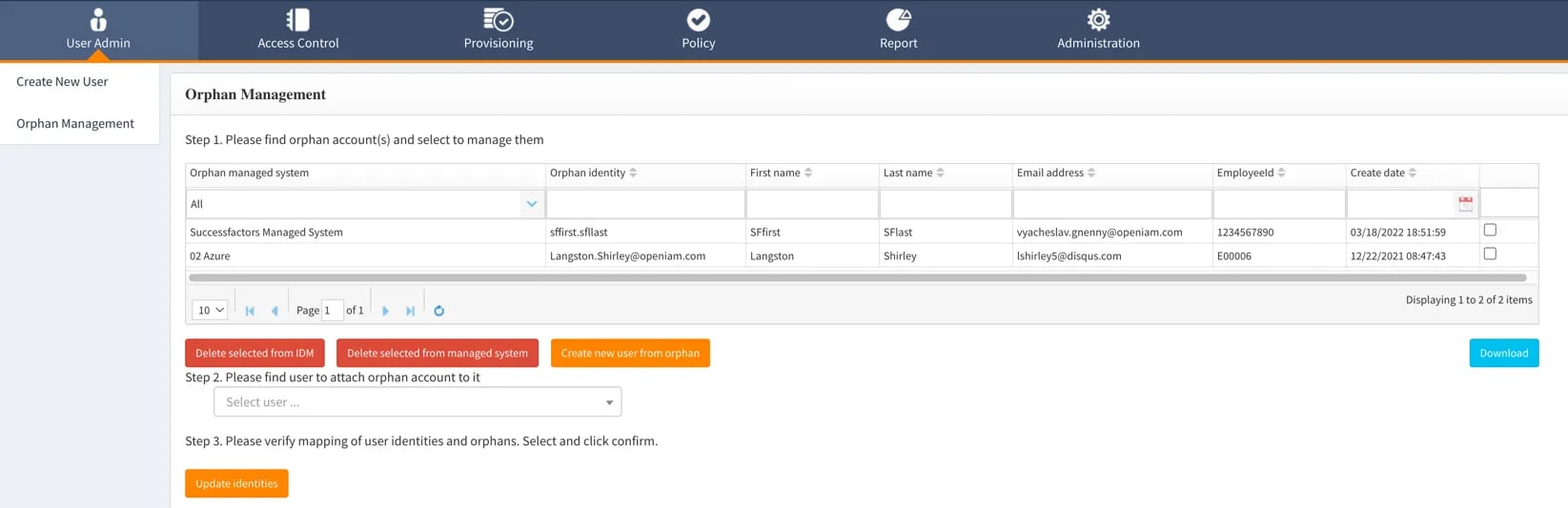
At some of our customers, they have a major cleanup effort ahead of them and they prefer to get a report which can be used to perform the cleanup. The report can be obtained using the blue download report button. For customers that are performing a manual cleaning of the target application, we can simply re-synch from the application. If an identity has been corrected and is no longer an orphan, it will automatically drop off from the orphan list.
In most cases, however, customers can use the interface shown above to perform one of the following operations on orphaned accounts:
- Link the orphaned account to a valid user
- Remove the orphan from OpenIAM
- Remove the orphan from the target application
Orphan management is designed to address a specific, but common, use case. Your feedback and questions are welcome.
FAQ - Frequently Asked Questions
What are orphaned accounts?
Orphaned accounts are user or machine identities that remain active in target systems after the person or service that owned them has left, changed roles, or no longer needs access.
Why are orphaned accounts dangerous?
They increase attack surface, allow privilege creep, and can be used by attackers or misconfigured automation to access sensitive systems. Orphans also create audit and compliance gaps.
How can I find orphaned accounts?
Use reconciliation and scheduled audits: compare authoritative identity sources (HR, AD, identity store) against target system accounts, look for stale last-login dates, disabled HR status, and accounts with no owner or no recent activity.
What immediate steps should we take when an orphaned account is found?
Isolate or disable the account, investigate recent activity, revoke credentials (API keys, tokens), update or remove service bindings, and then follow a remediation workflow (reassign, delete, or document exception).
How does automation help manage orphaned accounts?
Automation (reconciliation, JML flows, policy rules) detects orphans regularly, flags or remediates them automatically, and keeps target systems aligned with governance policies — reducing manual effort and time to remediate.
What are best practices to prevent orphaned accounts long-term?
Enforce HR authoritative data as source of truth, implement JML lifecycle automation, run periodic reconciliations, apply access certification, require account ownership, rotate credentials, and document exception workflows.
